Configuring Internet Firewall Rules for Microsoft Teams Direct Routing
Introduction
This is the fourth in a series of articles on hardening AudioCodes Session Border Controllers (SBCs). The series is mostly following the guidance provided by AudioCodes. These configuration notes are referenced at the end of this article. These articles are components of eGroup | Enabling Technologies’ security mantra:
We are going to look at the rules that need to be added to an organization’s internet-facing firewall to provide connectivity between Microsoft Teams and AudioCodes SBCs configured to support Teams Direct Routing:
Background
In the previous article in this series, Separation of Un-trusted Network Traffic on AudioCodes SBCs, we talked about the concept of trusted and untrusted interfaces on an AudioCodes SBC. Most SBCs will have:
It is a well-accepted and understood practice to deploy a firewall solution between the internet and an organization’s DMZ and trusted networks. The main purpose of a firewall is to block all inbound traffic from the internet while only allowing permitted bidirectional traffic to be routed to the organization’s DMZ and trusted networks.
Dedicated circuits or direct connections between an organization and a vendor usually bypass the organization’s internet firewall. Most SIP Trunk vendors when implementing a dedicated SIP Trunk circuit will install their own SBC(s) or SBC/firewall combination on the organization’s premises. The vendor SBCs are then cross-connected to an untrusted interface on an AudioCodes SBC over a small, dedicated network with between two (2) and four (4) endpoints. Hardening the SBC protects it from unwanted traffic coming from the vendor’s equipment much like the organization’s own internet firewall.
Microsoft Teams Direct Routing Firewall Requirements
The firewall requirements for the different Microsoft and Office 365 tenants can be found on the Plan Direct Routingweb page. For each type of tenant, the web page provides the:
***These are not the firewall requirements for Microsoft Teams traffic. These can be found on the Office 365 URLs and IP address ranges web page.
On Windows Servers running the Azure Monitor Agent, use data collection rules to define the data to collect from each agent. Besides for the predefined sets of events that you can select to ingest, such as All events, Minimal, or Common, data collection rules enable you to build custom filters and select specific events to ingest. The Azure Monitor Agent uses these rules to filter the data at the source, and then ingest only the events you’ve selected, while leaving everything else behind.
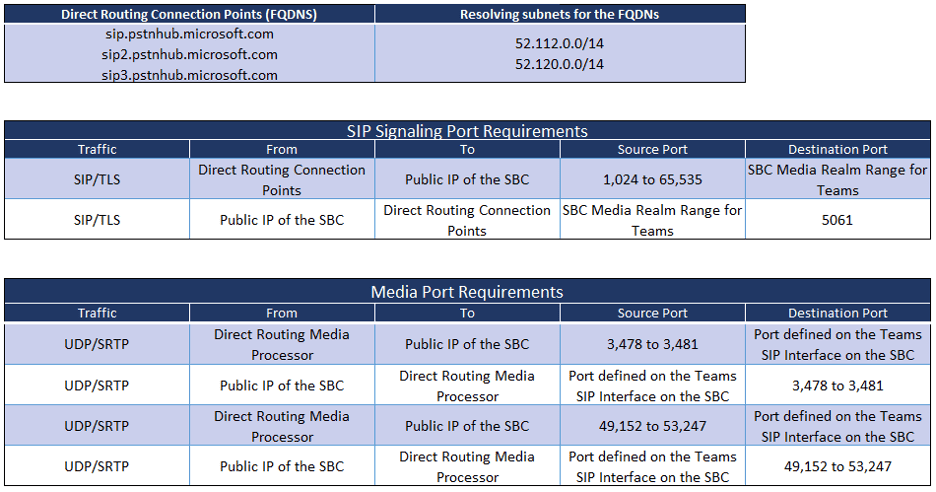
Microsoft 365, Office 365, and Office 365 GCC Tenants
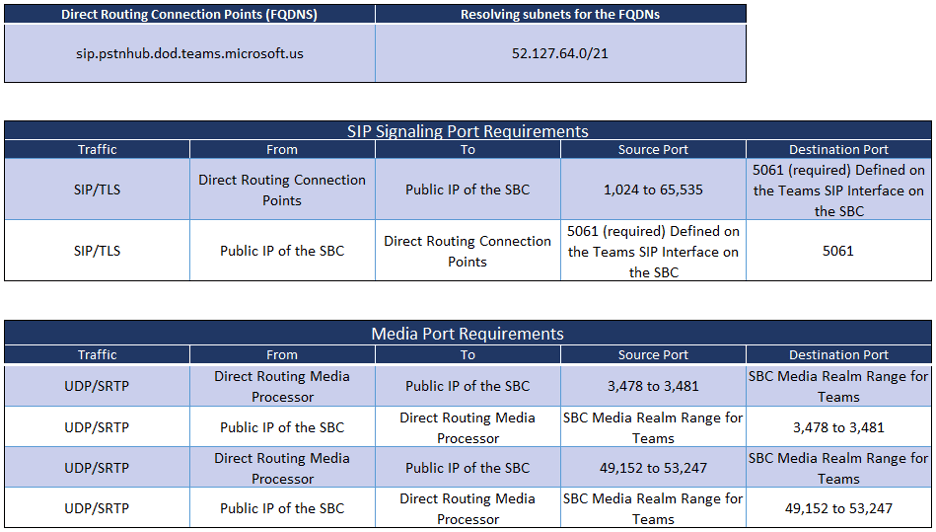
Microsoft Office 365 DOD Tenants
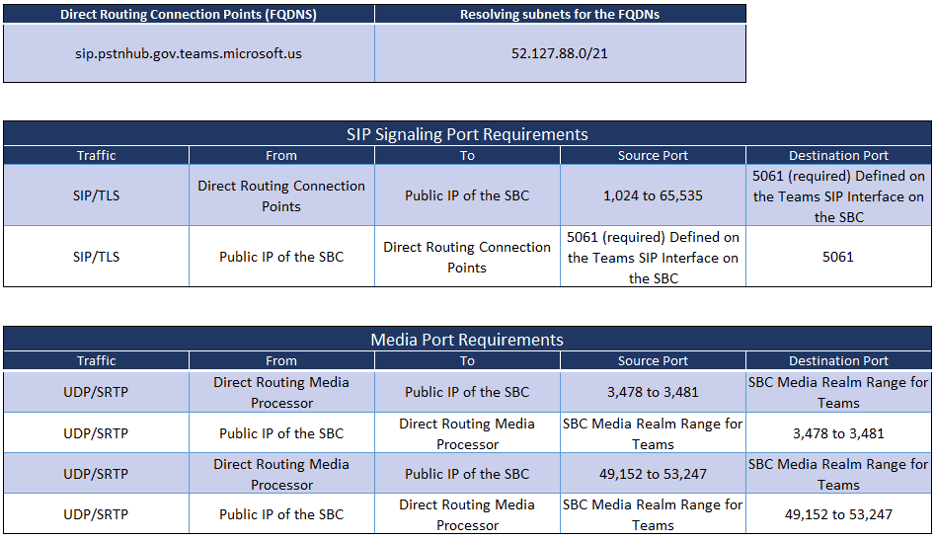
Microsoft Office 365 GCC High Tenants
Teams Media Port Ranges and Media Realms on the SBC
In a previous article in this series, Separation of Un-trusted Network Traffic on AudioCodes SBCs, the physical and logical separation of the SIP traffic traversing the SBC was discussed. On the logical side, we talked about each SIP service (Teams, SIP Trunks, ERSPs, etc.) having its own set of defined parameters. Each SIP service on the SBC should have its own:
In terms of the organization’s internet firewall rules the two (2) SBC elements that come into play are the Media Realms and the SIP Interfaces. A Media Realm defines a specific range of UDP ports to be used for SIP Media traffic. Media Realms are in turn assigned to SIP Interfaces and IP Groups. Each SIP service should have its own Media Realm, SIP Interface and IP group.
SIP signaling traffic is usually configured on ports in the 5060 to 5075 range. To avoid these ports, the default starting port for SIP media on an AudioCodes SBC is 6,000 with the available ports extending to 65,535. When defining a Media Realm port range, you need to specify the starting port and number of media session legs. The ending port is calculated based on these inputs. We are not going to dive deeper into the nuances of configuring Media Realms in this document. Typical practice is to separate the starting ports of the ranges by 1,000 and configure 100 media session legs. Each of these ranges would have 1,000 ports and no overlapping. This is assuming that the “UDPPortSpacing” parameter on the SBC is set to ten (10).
On a new SBC, the Media Realm for the LAN (trusted) interface would usually start at port 6,000 and extend to 6,999. If Teams is the first SIP service added to the SBC, the ports in its realm should be from 7,000 to 7,999. It is this range that is referred to as the “SBC Media Realm Range for Teams” in the tables above. In the tables, 7,000-7,999 can be inserted in the cells that currently say, “SBC Media Realm Range for Teams”.
The next SIP service added to the SBC will have its Media Realm setup for ports 8,000 through 8,999.
Teams Media Bypass and Teams Local Media Optimization (LMO)
Teams Media Bypass and Teams Local Media Optimization (LMO) are optional features that can be enabled on Direct Routing SBCs. Both reduce the number of hops and improve performance for SIP Media traffic between Teams endpoints and the Session Border Controller. Enabling Media Bypass requires the addition of several more firewall rules. LMO requires the same set of rules on the organization’s internet firewall. If there is a firewall between the internal endpoints and the trusted interface of the SBC, additional rules may need to be added to this firewall.
Microsoft 365, Office 365, and Office 365 GCC Tenants
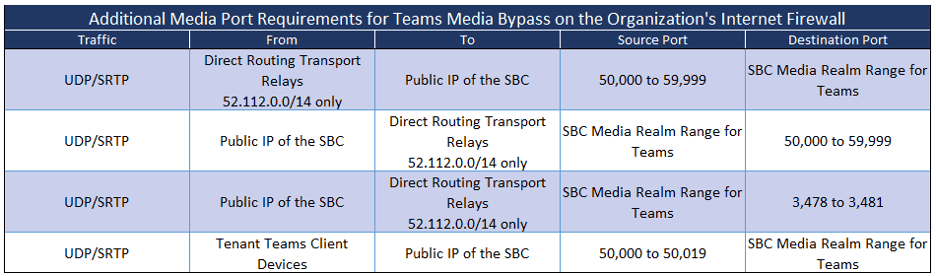
Microsoft Office 365 DOD Tenants
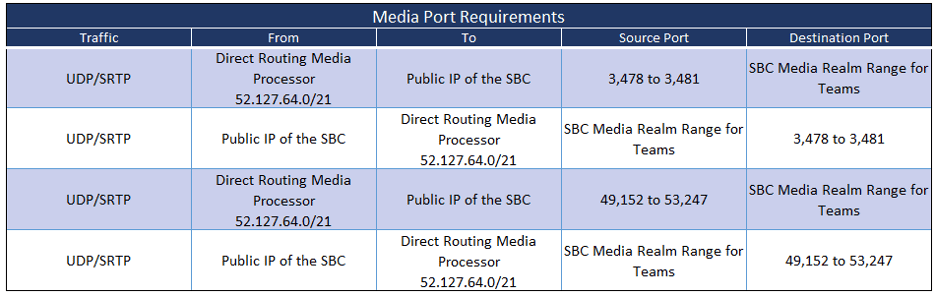
Microsoft Office 365 GCC High Tenants
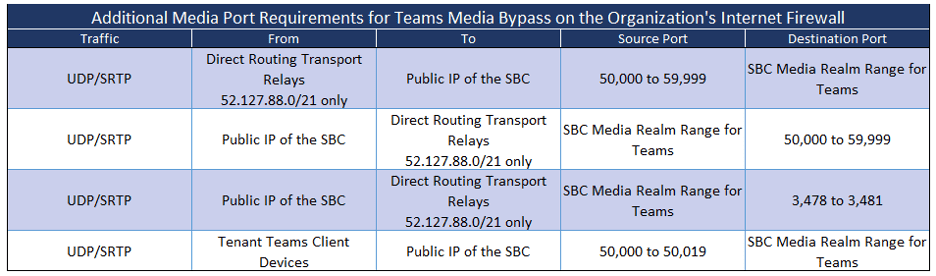
Firewall Rules for SIP Trunks, ERSPs and other SIP Entities
Summary
eGroup | Enabling Technologies is available and ready to answer any questions that you might have about defining the required organizational internet firewall rules for Teams Direct Routing. While we did not go into Media Bypass and Local Media Optimization in depth, we are ready to show you how these features can improve the performance of SIP media for your Direct Routing users.
This series is part of our effort to help our customers implement a “Trust No One and Harden Everything” security infrastructure. If you need help in implementing Teams Direct Routing or a security infrastructure for your organization, please contact us!
Bibliography
AudioCodes has written documents addressing security on their Session Border Controllers and Gateways. There are versions for the 7.2 and 7.4 firmware in which they discuss the importance of setting up the SBC’s firewall rules:
The AudioCodes SBC user manuals can also be found in the Library section of the AudioCodes website.

Cloud Solutions Architect - eGroup | Enabling Technologies