

Senior Cloud Solutions Architect
Insider risks are a growing threat to organizations, especially in the era of remote work and cloud-based services. Insider risks can be caused by malicious actors who intentionally steal or leak sensitive data, sabotage systems, or compromise accounts. They can also be caused by negligent or compromised users who accidentally or unknowingly expose data, violate policies, or fall victim to phishing or malware attacks.
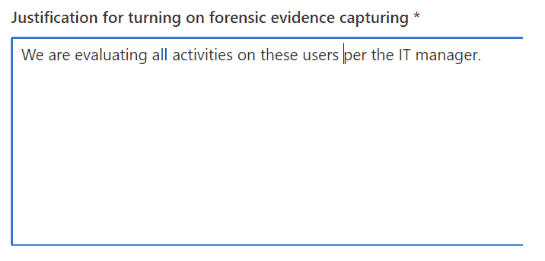
To effectively manage insider risks, organizations need to have a comprehensive solution that can monitor user activity, detect anomalous behavior, alert security teams, and respond to incidents. Moreover, they need to have a reliable way to collect and preserve forensic evidence that can support investigations and legal actions.
In this blog post, I will show you how to configure Purview Insider Risk Management to collect forensic evidence on managed devices enrolled in Intune. I will demonstrate how to use Microsoft Intune to install the agent required to capture forensic evidence on enrolled Windows devices.
Purview Insider Risk Management (IRM) is a cloud-based compliance solution designed to help organizations detect, investigate, and act on malicious and inadvertent activities that pose insider risks. It correlates various signals to identify potential risks such as intellectual property theft, data leakage, and security violations. IRM leverages advanced analytics, machine learning, and user and entity behavior analytics (UEBA) to monitor user activity across various data sources, such as Microsoft 365, Azure, SharePoint, OneDrive, Teams, Exchange, and more.
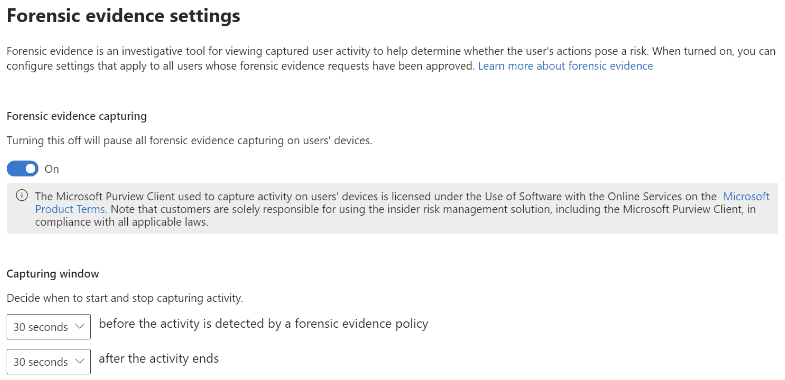
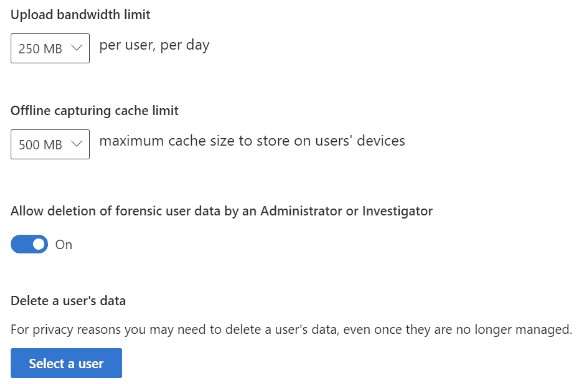
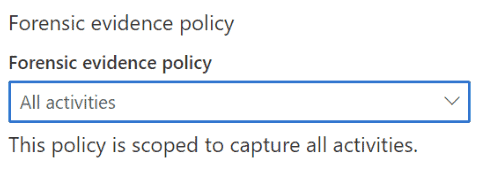
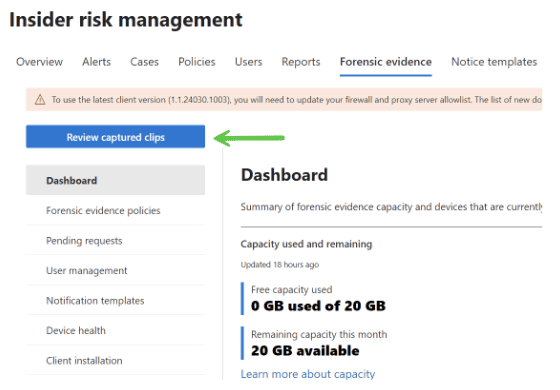
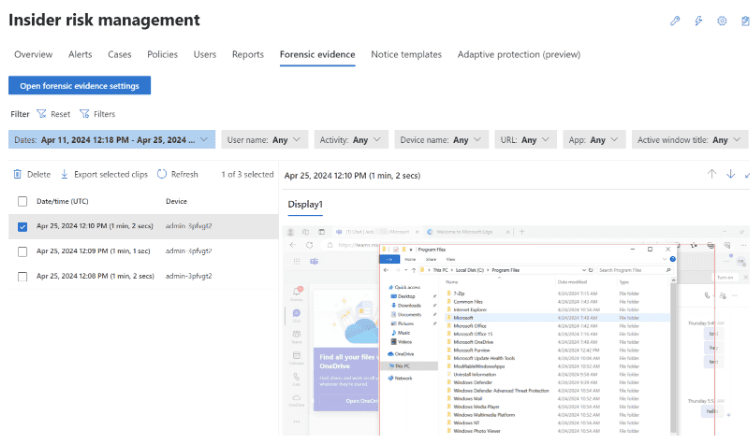
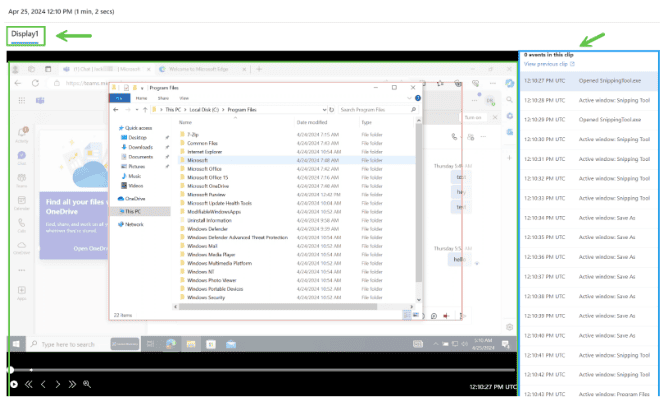
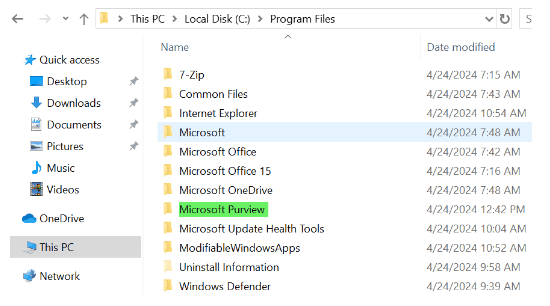
IRM Forensic Evidence provides security teams with visual insights into potential insider data security incidents. It includes customizable event triggers and built-in user privacy protection controls, providing a thorough investigation path to insider data risks, such as unauthorized data exfiltration of sensitive information.
Purview Insider Risk Management can help you:
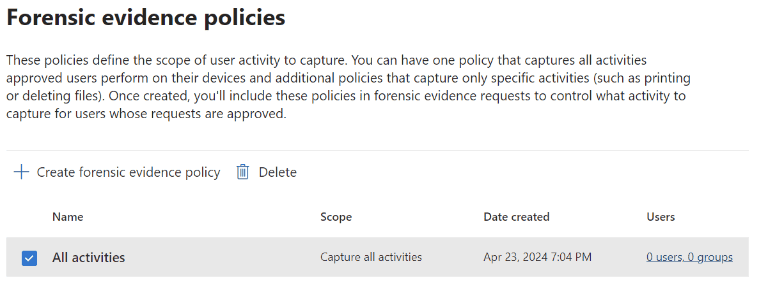
In addition to the capabilities outlined above, adding Forensic Evidence to IRM can provide additional visual context to security teams aiding their investigations. Activities such as printing files, creating, or copying files to USB, creating, or transferring files to a network share, and even using a browser to upload files to the web.
Licensing:
Supported Platforms:
Hardware | Minimum Requirement |
RAM | Minimum of 8 GB (at least 2 GB should be available for client usage) |
CPU | Intel i5 or above and AMD Ryzen 5 or above |
Graphics | Compatible with DirectX 11 or later, with a WDDM 1.0 driver or later (currently only integrated graphics cards supported) |
Disk | Minimum of 10 GB of disk storage |
Display | Minimum screen resolution of 1920 x 1080 |
Virtual Devices:
Hardware | Minimum Requirement |
RAM | Minimum of 16 GB (at least 2 GB should be available for client usage) |
CPU | Minimum of eight vCPU processors or equivalent |
Disk | Minimum of 10 GB of disk storage |
Display | Minimum screen resolution of 1920 x 1080 |
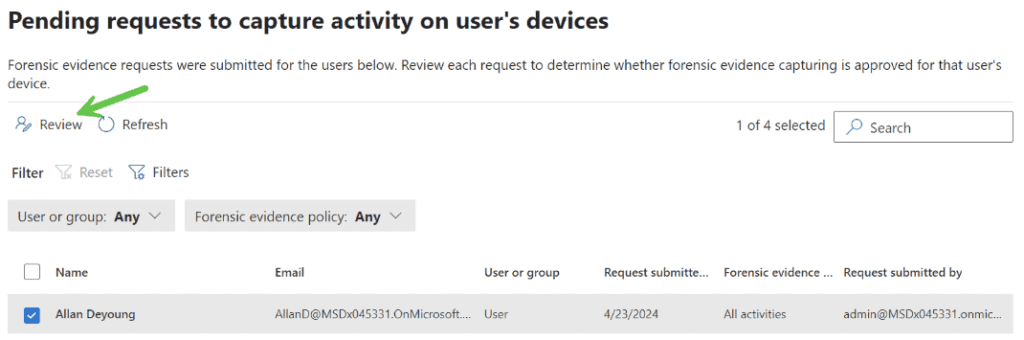
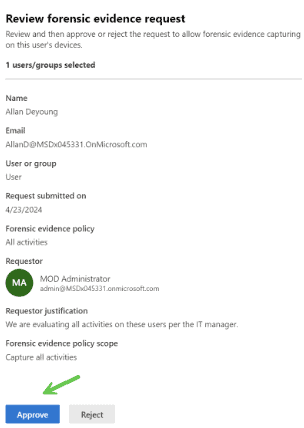
Permissions/Role Groups required for viewing, submitting, and approving forensic evidence. To assign these roles to users or groups, you need to use the Purview portal. To learn more about how to assign roles and manage permissions in Purview Insider, see the documentation here.
Purview Role Group | Capability |
Insider Risk Management | Configure and view everything inside IRM. |
Insider Risk Management Admins | Configure polices, access analytics insights and submit forensic capturing requests. |
Insider Risk Management Investigators | Access and investigate cases, alerts, and forensic evidence captures. |
Insider Risk Management Auditors | View & export audit logs. |
Insider Risk Management Approvers | Only review, approve, or reject forensic collection requests. |
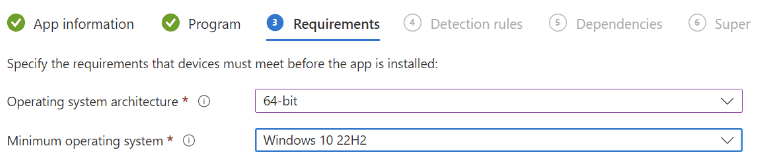
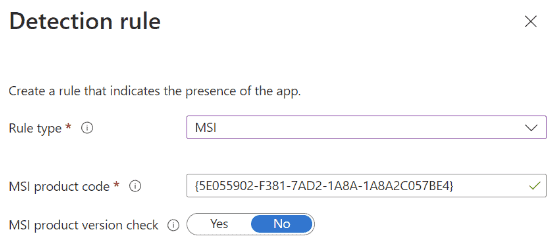
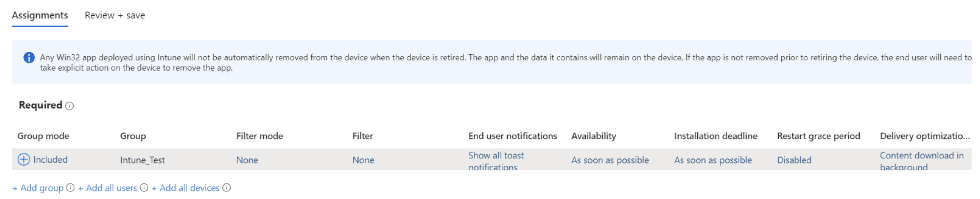
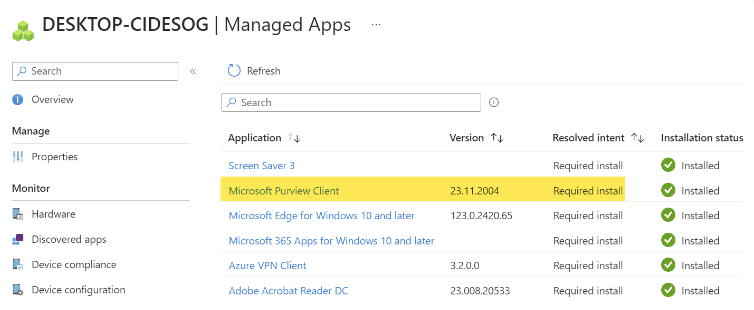
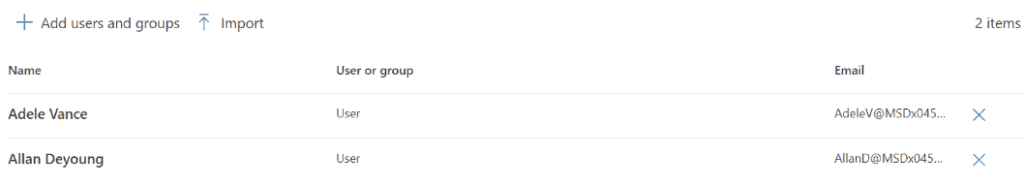
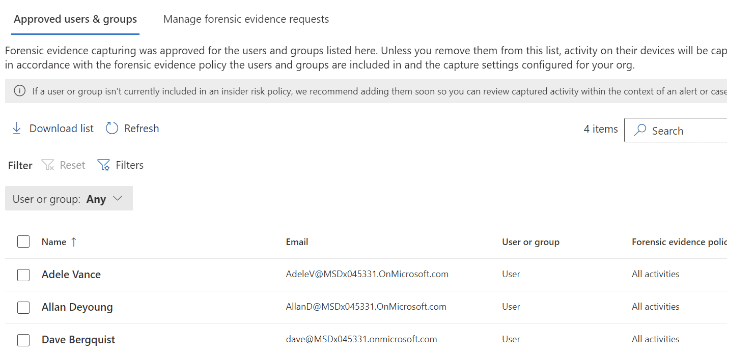
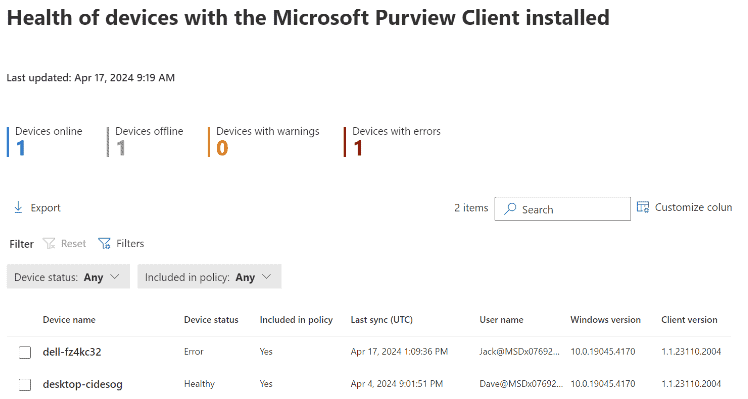
You must onboard devices to the Purview compliance portal and install the Purview agent to devices to start capturing content. For the purposes of this article, we will onboard devices via the Purview compliance portal and use Microsoft Intune to push out and install the Purview Forensic client. We will download the Purview client, wrap it with the Microsoft Win32 Content Prep Tool (Intunewin), and push the packaged client out to the intended devices. The client will be used to onboard and capture activity on approved users’ Windows devices.
Onboard device via the Purview Portal: Settings -> Device onboarding -> Devices and onboard your devices. It may take a couple of hours before devices show up.
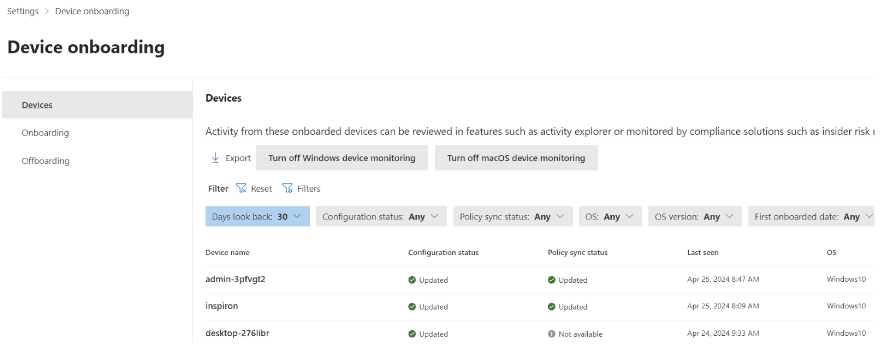
Download the Purview Forensic client.
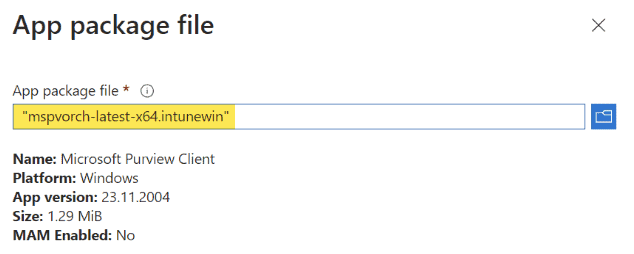
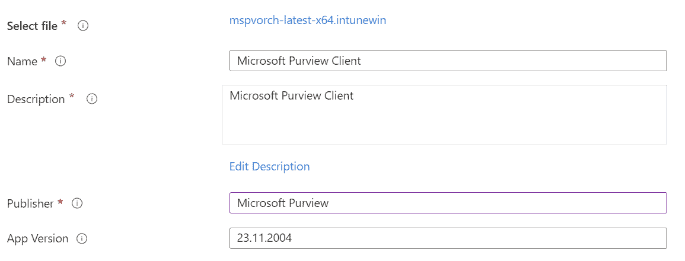
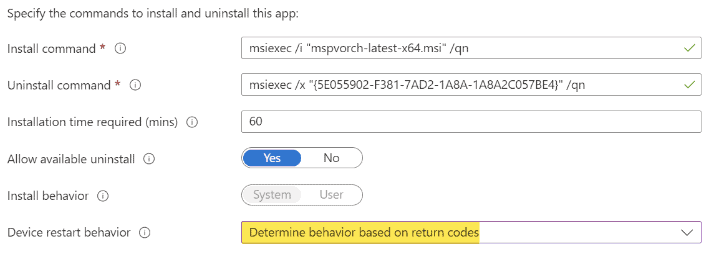

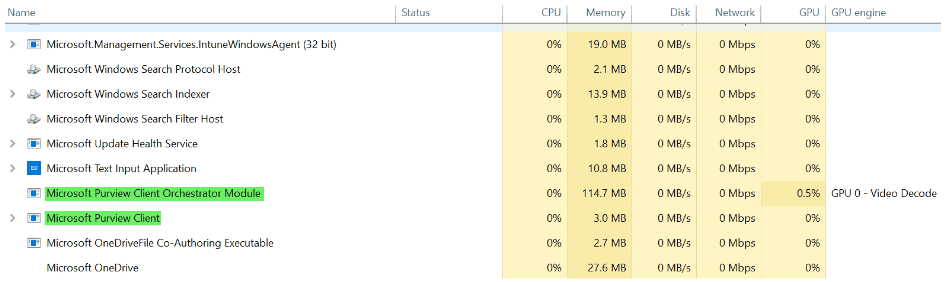
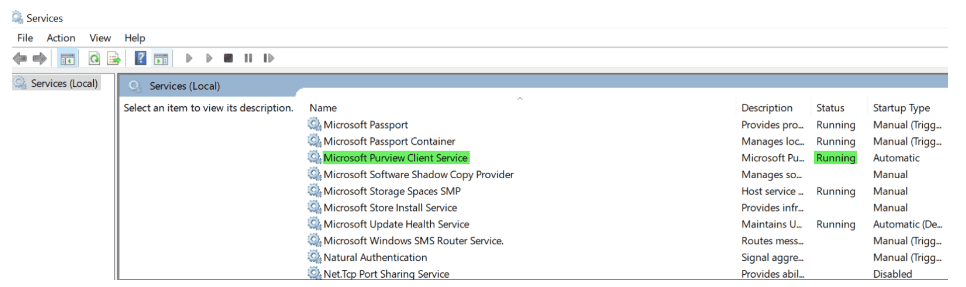
Insider risks are a serious challenge for organizations, and they require a comprehensive and effective solution. Purview Insider and Intune can provide you with such a solution, by helping you monitor user activity, detect insider threats, alert and respond to incidents, and collect and preserve forensic evidence. By integrating Purview Insider and Intune, you can enhance your insider risk management capabilities and protect your organization from insider threats.
We hope you found this blog post helpful and informative. If you have any questions, feedback, or require assistance, please contact us here or complete the form below. Thank you for reading!
Contact our team of experts today to discuss how to better secure your data!