

Senior Cloud Solutions Architect
Endpoint Privilege Management is a crucial aspect of IT security and compliance. It involves granting the minimum level of permissions and privileges necessary for devices and users to perform their tasks, while preventing unauthorized or malicious actions. Endpoint Privilege Management can help reduce the risk of data breaches, malware infections, ransomware attacks, and other cyber threats.
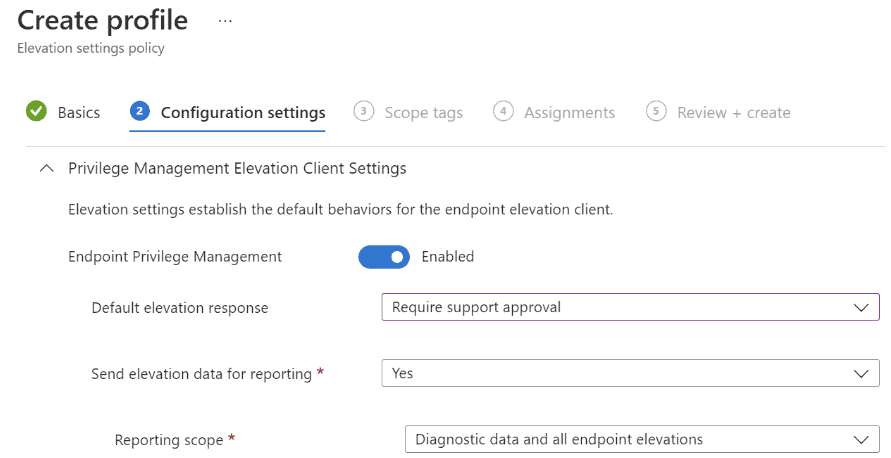
The purpose of this article is to show you how to deploy and manage Microsoft Intune Endpoint Privilege Management (EPM) for standard users, along with showing the end user and administrator experiences throughout the process for a single application. As a user needs to install an application, they will be required to request elevated access. Once an administrator approves, they will be notified that the application is available to install with elevated privileges. I will also demonstrate how to see if the user installed the application using Microsoft Intune device query. Microsoft Intune EPM and Device Query are part of the Microsoft Intune Suite add-on licensing.
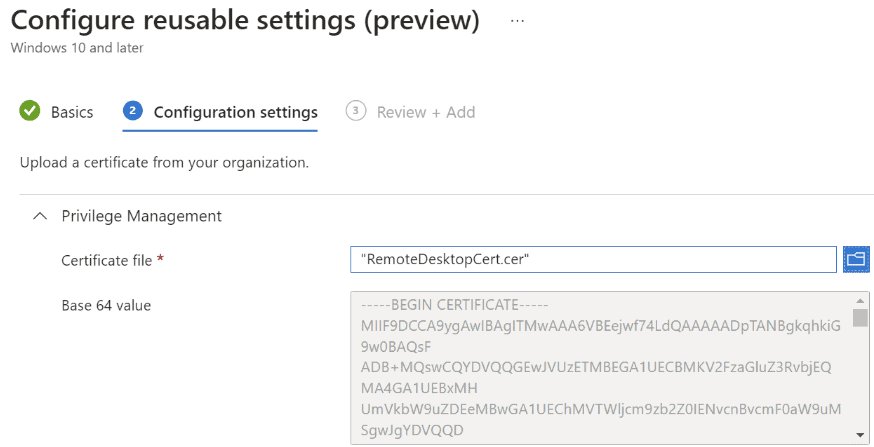
To deploy Microsoft Intune EPM, you will need the following:
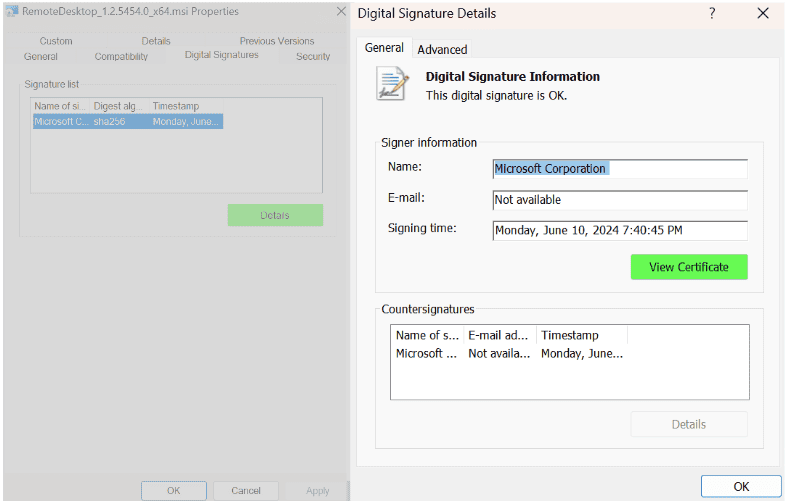
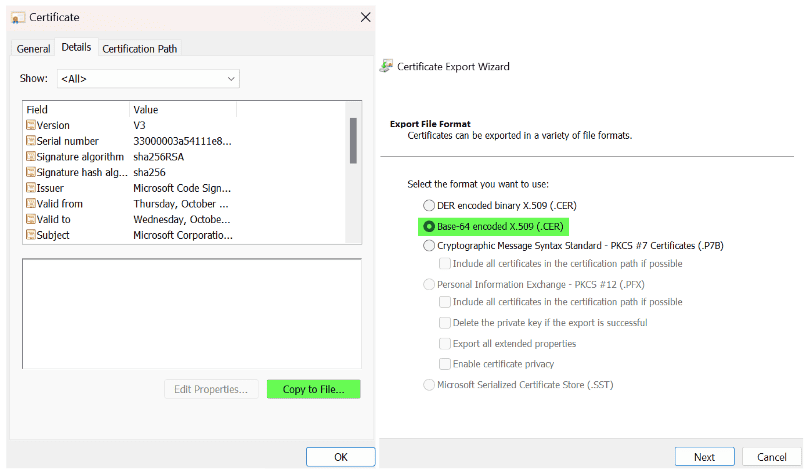
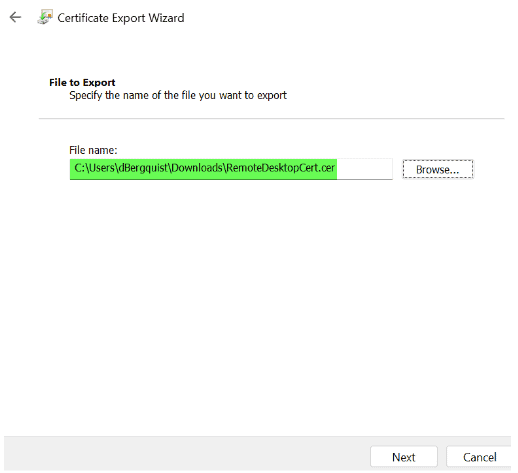
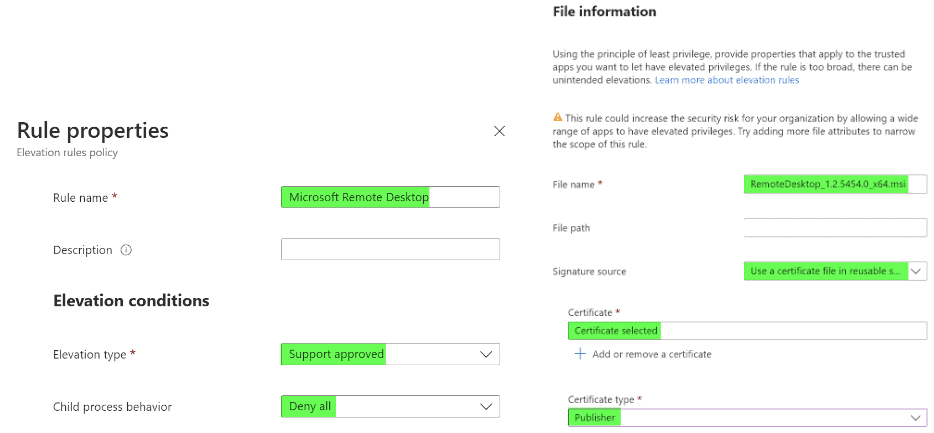
We will be walking through the Microsoft Intune EPM configuration targeting the Microsoft Remote Desktop application. However, you can apply similar principles to your own applications.

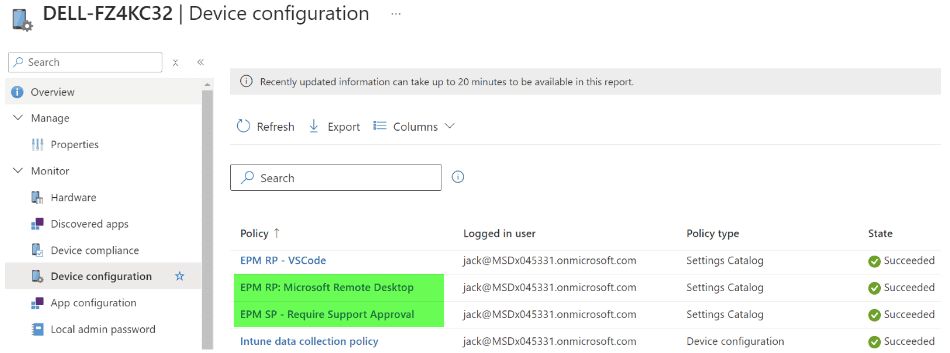
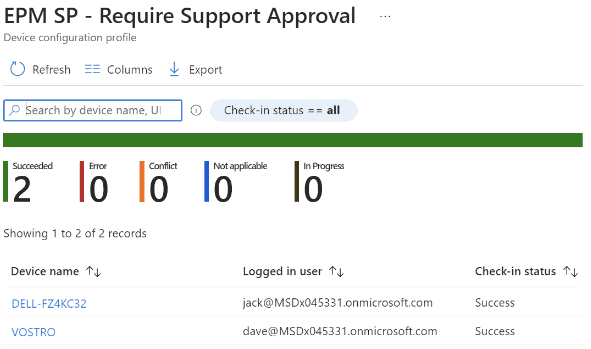
2. You can also monitor by the policies themselves: Endpoint Security -> Endpoint Privilege Management -> select a policy -> View report.
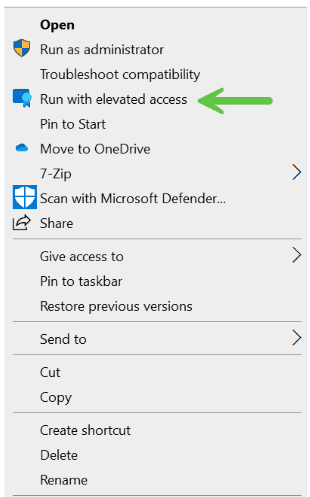
An end user can request access to install the Microsoft Remote Desktop application by right clicking the file and selecting the “Run with elevated access” option.
Before Microsoft Intune EPM is applied: Access should be denied for standard users until approval has been given.
After Microsoft Intune EPM is applied: Will allow the user to request access and install once an administrator approves. The end user will get a Windows toast notification once approved. This could take 15 minutes, give or take.
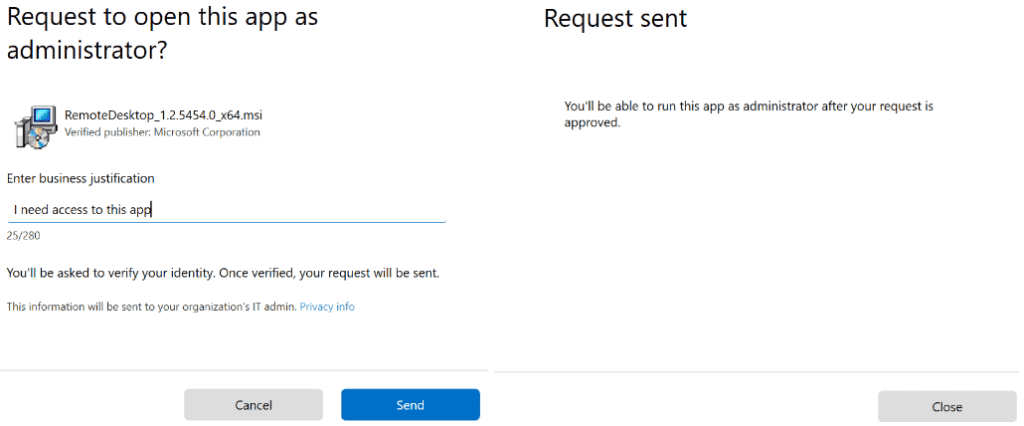
Business Justification: Once the end user runs the application with elevated access, they will be required to provide a business justification.
User Notification: Once the administrator approves the request, the user will receive a Windows toast notification that they can now run the application with elevated access.
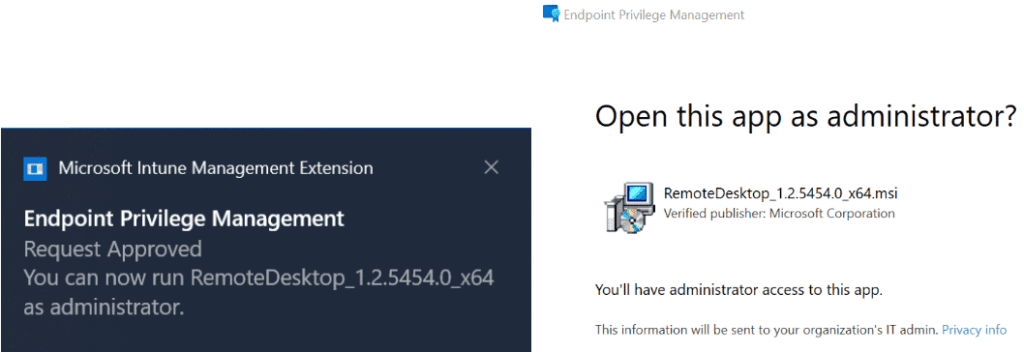
Administrators must use the “Elevation Requests” tab to view pending requests. Currently, they do not get notified by any other means.
View elevation requests: Via the Microsoft Intune Administration portal, the administrator can go to: Endpoint Security -> Endpoint Privilege Management -> Elevation Requests:
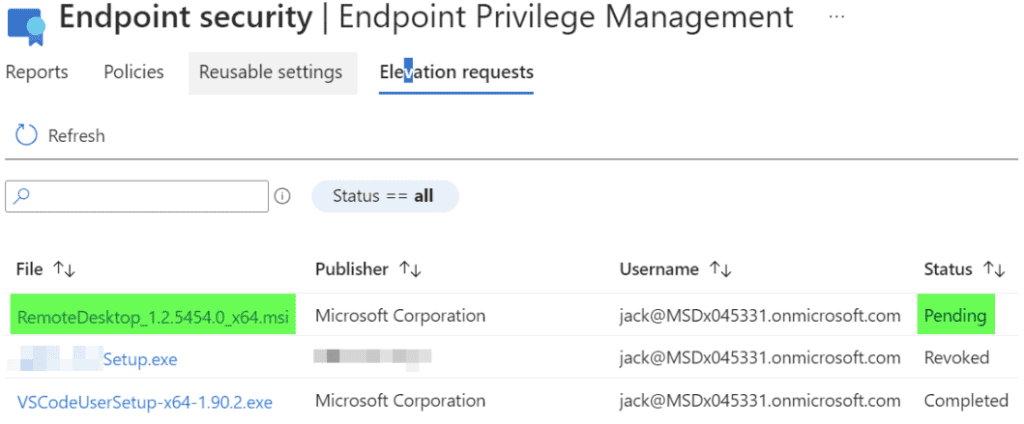
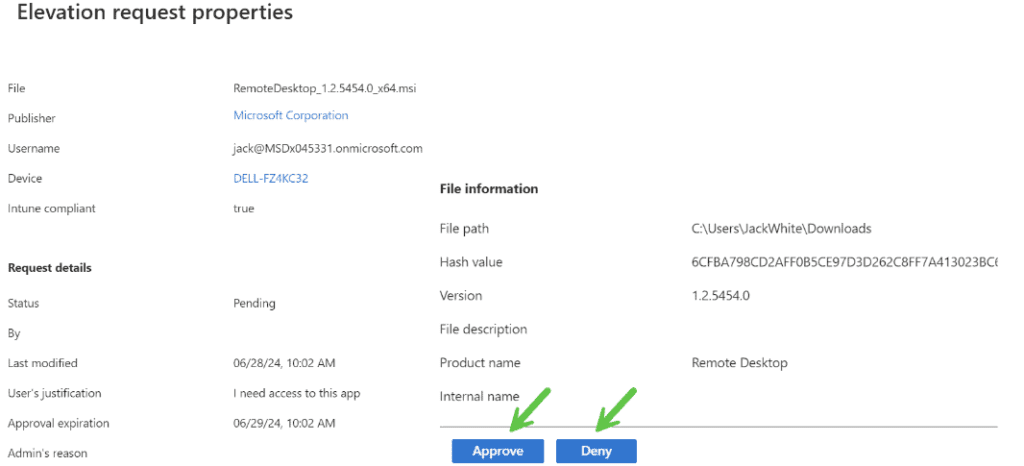
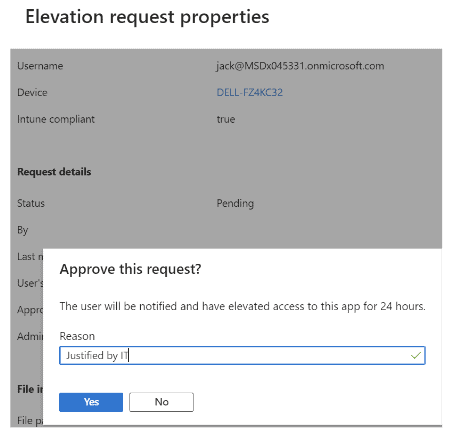
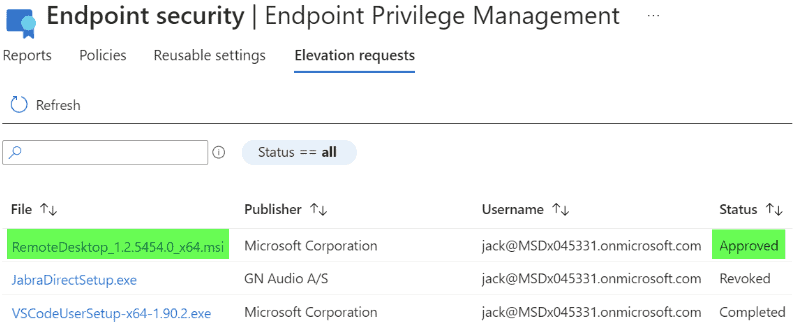
Approve, Deny, Revoke: An administrator can select the app and either approve or deny the initial request. You can also revoke access post approval.
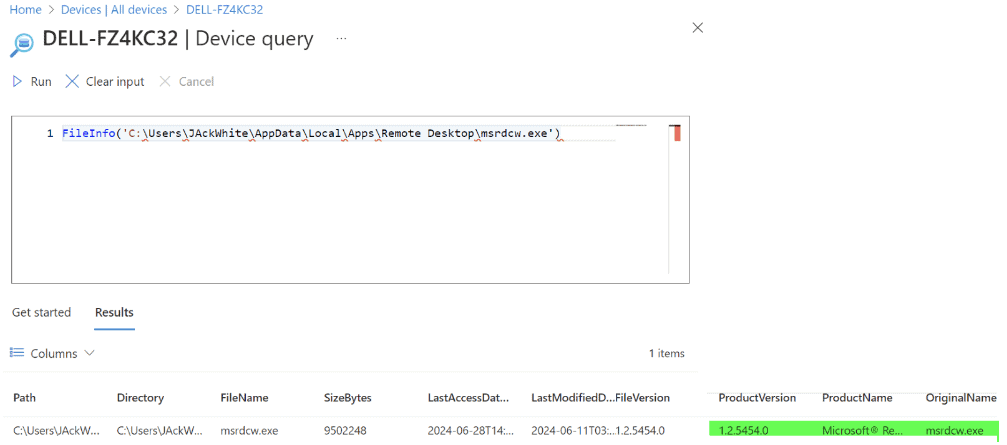
Device Query: An administrator can check to see if the application has been installed on the device using Microsoft Intune device query. In this example, we will check to see if the exact file is installed in the expected directory:
As you can see, the Microsoft Remote Desktop executable was discovered showing the application was installed.
By using Microsoft Intune Endpoint Privilege Management, IT administrators can achieve the following benefits:
Microsoft Intune Endpoint Privilege Management is a powerful and flexible solution that can help IT administrators control and monitor the access rights of devices and users, while ensuring security, compliance, productivity, and user experience. It can be easily configured and deployed from the cloud, and support a variety of devices, apps, and scenarios.
If you have any questions or are looking for assistance in creating a Modern Endpoint Management strategy or deploying Microsoft Intune Endpoint Privilege Management as part of your device management solution, please reach out to info@eGroup-us.com or complete the form below.
Contact our team today to schedule a call with one of our experts.