As cloud adoption accelerates, organizations must strengthen security to protect sensitive data and prevent cyber threats. Cloud Access Security Brokers (CASBs) provide visibility, compliance enforcement, and data protection—ensuring that cloud applications remain secure while preventing unauthorized access and data leaks.
See: Table of Contents
Cloud Access Security Brokers (CASBs)
A cloud access security broker (CASB) is an enterprise security solution designed to monitor cloud environments for exfiltration and other threats such as data breaches, unapproved use of unapproved applications, and DNS tunneling used by malicious actors to obscure Command and Control channels.
CASBs provide unparalleled visibility, compliance management, threat detection, and data protection capabilities that enable organizations to confidently embrace cloud technologies.

A Cloud Access Security Broker (CASB) is an enterprise security solution designed to monitor cloud environments for threats such as data breaches, unapproved applications, and DNS tunneling, which malicious actors use to obscure command-and-control channels.
CASBs provide:
- Unparalleled visibility into cloud environments
- Compliance enforcement for industry regulations
- Threat detection to mitigate cloud security risks
- Data protection capabilities to prevent unauthorized access
Summary: Why CASBs Matter
CASBs serve as an essential security layer in cloud environments, offering visibility, governance, and protection against evolving cyber threats.
Zero Trust Implementation and CASBs

As part of a Secure Access Service Edge (SASE) strategy, CASBs serve as security policy enforcement points between an organization’s on-premises infrastructure and cloud service providers. This ensures that security, governance, and compliance (SG&C) policies are applied consistently across an organization’s cloud environment.
See: Microsoft Zero Trust Framework
CASBs can assist organizations in discovering what data is distributed across their software-as-a-service (SaaS) applications, and how that data is utilized. Furthermore, these systems protect this information during transit between SaaS applications and an on-premises network by employing various encryption, tokenization, and DLP processes to prevent loss of sensitive information.
A key capability of CASB tools is their ability to detect and block unsanctioned use of SaaS applications by employees, commonly referred to as shadow IT, which poses serious threats to an organization’s security and compliance posture. By interjecting security policies as data travels from user devices to cloud servers, CASB tools can prevent activities that would violate an organization’s SG&C policies from taking place.
As most companies understand what data resides within their sanctioned cloud applications, they may not be as aware of what employees store and transfer using unsanctioned apps – an activity which poses a major threat to the security posture of an organization and must be managed if zero trust implementation is to remain successful. Centralized Access Security Brokers (CASBs), which have the ability to detect unsanctioned apps as well as monitor which data transfers between them, are integral components of such deployments.
A cloud application security and auditing (CASB) platform should offer not only visibility into all the applications used within an organization, but also advanced capabilities to protect against security threats. These include threat protection, configuration management, and user behavior analytics.
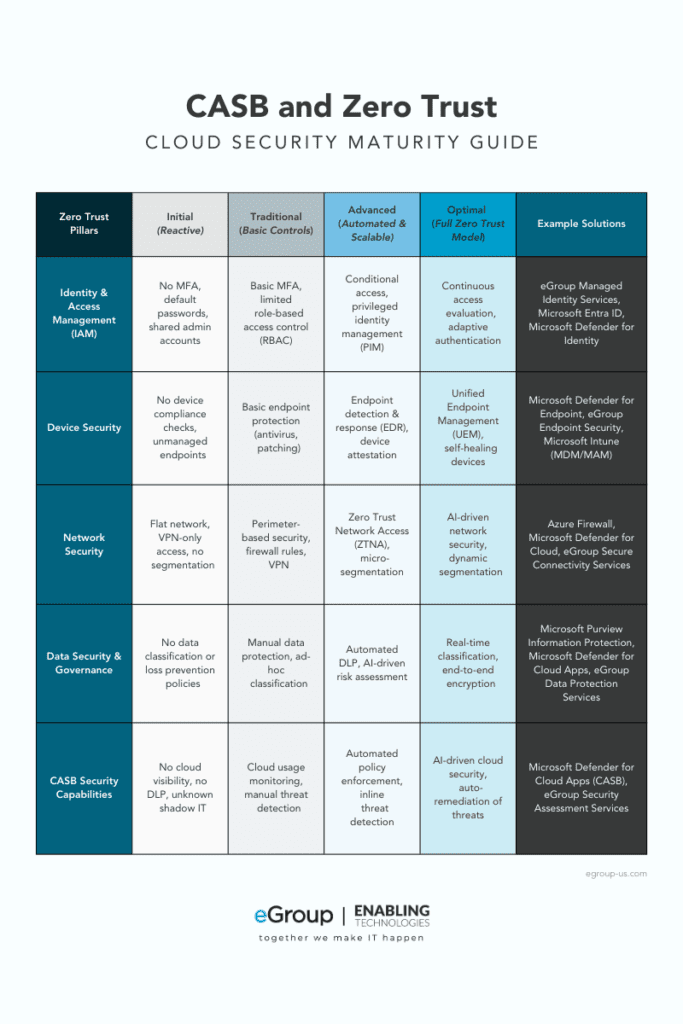
When selecting a CASB for your organization, it is essential that it meet the pillars of zero trust implementation:
Establishing an attack surface should be the cornerstone of any zero trust strategy. This involves identifying your most valuable digital assets – from sensitive employee or customer data to proprietary business information – as well as any critical applications used in your business, such as point-of-sale terminals, Internet of Things devices, or medical equipment.
eGroup provides comprehensive CASB protection through our Enabled Security services. Our solution is designed to deliver scalable, enterprise-grade security while ensuring seamless cloud adoption. eGroup’s ThreatHunter MXDR continuously monitors for threats such as ransomware and insider risks, allowing businesses to detect and mitigate security issues before they escalate.
Key functions of CASBs in Zero Trust security:
- Data Discovery: Identifies how data is stored, accessed, and shared across SaaS applications
- Encryption & Tokenization: Protects sensitive data during transmission
- DLP (Data Loss Prevention): Prevents unauthorized file sharing and data exfiltration
- Shadow IT Detection: Blocks unauthorized applications that could compromise security
🚨 Shadow IT Risk: Many organizations don’t realize how much sensitive data is being stored in unsanctioned applications. CASBs detect these applications and prevent unapproved data transfers, ensuring Zero Trust security principles are upheld.
Summary: How CASBs Strengthen Zero Trust
CASBs detect and block unsanctioned cloud applications while enforcing security controls across cloud environments, making them a key enabler of Zero Trust strategies.
Privileged Identity and Access Management

Key to any CASB solution is its Privileged Identity and Access Management (PIAM) model, which allows businesses to manage cloud application access across both managed and unmanaged devices. By implementing a CASB, security teams can enforce precise access regulations that prevent unauthorized data sharing or leakage.
This is achieved by identifying privileged identities, securing their credentials in a vault, and enforcing least privilege policies to ensure users and third parties only receive the access they need. Continuous monitoring of privileged access activities and remote sessions helps detect malicious behavior and apply security controls effectively.
PIAM also enhances data governance by allowing organizations to implement tailored policies, such as blocking, alerting, encryption, and quarantining of sensitive information. With deep visibility into cloud applications, CASBs help track user behavior, assess infrastructure risks, and defend against threats like stolen credentials or insider attacks. This ensures businesses can benefit from cloud applications while maintaining compliance with regulations like GDPR and HIPAA.
Beyond privileged access management, CASBs play a crucial role in controlling shadow IT. As employees increasingly use personal devices and unsecured Wi-Fi, CASBs help enforce security policies. By detecting and blocking risky applications, CASBs prevent unauthorized software from being installed on unmanaged devices, reducing the risk of data breaches.
CASBs also provide advanced threat detection by using device fingerprinting, data tracking, and malware analysis to identify suspicious activity. This enables security teams to act immediately when a threat arises, minimizing potential damage.
Additionally, CASBs integrate with identity and access management (IAM) solutions, ensuring that new users and devices are authenticated and granted appropriate permissions. This integration is a critical component of Zero Trust security, reinforcing access control and ensuring data protection across cloud environments.

A CASB’s privileged identity and access management (IAM) model enables organizations to manage access to cloud applications from both managed and unmanaged devices. This ensures that only authorized users and roles have access to sensitive systems.
Core components of Privileged Identity and Access Management within CASBs:
- Privileged Identity Discovery – Identifies and secures privileged accounts
- Vaulting Credentials – Stores sensitive credentials securely
- Least Privilege Access – Grants only necessary permissions for tasks
- Session Monitoring – Detects and responds to privileged access abuse
CASBs also support deep visibility into user activity, helping organizations track behavior, assess infrastructure risks, and detect insider threats.
Summary: Why IAM Matters in CASBs
Strict access controls and continuous monitoring prevent unauthorized privilege escalation and mitigate security risks in cloud applications.
Eliminating Data Exfiltration Outside of Your Organization

Cloud applications offer scalability and flexibility, but they also introduce new security challenges that traditional perimeter-based defenses fail to address. Cyber threats such as malware, insider risks, and unauthorized data transfers require a more dynamic security approach—one that cloud access security brokers (CASBs) are designed to provide.
A CASB acts as a cloud security guardian, monitoring all devices and networks to ensure sensitive data remains protected, even outside traditional security perimeters. Additionally, CASBs help businesses optimize cloud service usage by identifying unnecessary licenses and tracking costs.
One of the primary benefits of CASBs is preventing data leaks. Organizations can establish security policies that detect and restrict sensitive file transfers, alerting administrators when an employee attempts to upload or download protected information. In cases of policy violations, CASBs can block access or enforce encryption to stop unauthorized exfiltration.
Beyond access control, CASBs leverage advanced analytics to strengthen data protection. By continuously monitoring user behavior, access patterns, and device activity, they establish a baseline of normal operations and flag suspicious deviations—potentially indicating malware infiltration or hacking attempts. This proactive approach allows security teams to detect threats before they escalate.

CASBs also enforce compliance policies across all cloud applications, ensuring both managed and unmanaged cloud services adhere to security best practices. Whether for file sharing, storage, or collaboration tools, CASBs help organizations maintain Zero Trust security principles and prevent unauthorized data exposure.
While cloud applications improve scalability, they also introduce new security challenges. Traditional perimeter-based security does not account for malware, insider threats, or unauthorized data movement within cloud environments.
How CASBs Prevent Data Leaks and Exfiltration
- Policy Enforcement – Blocks unauthorized file transfers
- Anomaly Detection – Identifies suspicious user behaviors
- Data Encryption – Secures files at rest and in transit
- Access Control – Restricts access to sensitive data based on role and device
Advanced CASB analytics help detect early indicators of malware, compromised credentials, and insider threats before they escalate into security incidents.
Summary: Stopping Data Breaches at the Source
CASBs enforce strict data access policies and detect unusual behavior, significantly reducing the risk of data leaks and cyber threats.
Final Thoughts: Why CASBs Are Critical for Modern Cloud Security
A Cloud Access Security Broker (CASB) is no longer an optional security tool—it’s an essential part of any Zero Trust or cloud security strategy. By implementing a CASB solution, organizations can:
- Gain full visibility into cloud applications and user behavior
- Prevent unauthorized access and privilege escalation
- Detect shadow IT and block unsanctioned cloud usage
- Enforce data loss prevention (DLP) and encryption policies
- Strengthen compliance with regulatory frameworks such as GDPR, HIPAA, and PCI DSS
For businesses embracing the cloud, CASBs provide a unified security approach that ensures data protection, compliance, and risk management—all while enabling secure, scalable cloud adoption.
Secure Your Cloud with eGroup
Looking to enhance your cloud security strategy? eGroup’s Cloud Security Services and Zero Trust Solutions can help you implement the right CASB framework tailored to your needs.
Contact Us for a security assessment, or explore our Managed Security Services to protect your cloud infrastructure today.








