Session hijacking attacks are evolving, and Microsoft Entra ID security must evolve too. Attackers are bypassing MFA using token theft, requiring businesses to adopt Conditional Access, risk-based authentication, and Zero Trust security measures. Learn how Microsoft’s 2025 updates address these threats.
- This is the 2025 update to our 2022 post, “MFA is (Unconditionally) Not Enough” – if you’re looking for the latest security insights, read on!
Microsoft Entra ID Security: Why MFA Alone Is Still Not Enough

Multifactor Authentication (MFA) is no longer enough to stop modern cyberattacks. While MFA remains a critical layer of security, attackers continue to exploit session hijacking and token theft to bypass authentication controls.
Microsoft has introduced new Conditional Access capabilities in Microsoft Entra ID to combat these threats—but many businesses haven’t fully implemented them. This 2025 update explains:
- Why session hijacking remains a top cyber threat
- How attackers bypass MFA with stolen tokens
- New Microsoft Entra ID Conditional Access updates in 2025
- Actionable steps to secure your business
If you’re still relying on MFA alone, it’s time to rethink your identity security strategy.
The Growing Threat: How Attackers Are Still Bypassing MFA in 2025
The Attack Breakdown
1) The Phishing Trap
- The attacker sends a fake Office 365 login page with a slight typo in the URL.
- Users enter their credentials, believing it’s legitimate.
2) Session Token Theft
- If the victim is logged into Office 365, the fake site captures their authentication token.
- This allows the attacker to reuse the session—bypassing MFA entirely.
3) Impersonation & Fraud
- They impersonate the victim to request wire transfers or distribute further phishing emails.
- Attackers access the victim’s email and sensitive data.

- In 2025, Microsoft has introduced better session protection—but businesses must enable and configure these features correctly. Get in touch with us for more information on setting these up!
2025 Update: Microsoft Entra ID Conditional Access Enhancements
New in 2025: Stronger Conditional Access Controls
Microsoft has expanded Conditional Access capabilities in Microsoft Entra ID, improving security against token theft attacks.
| New Conditional Access Features | How They Stop MFA Bypass |
|---|---|
| Token Protection for Microsoft 365 | Prevents session tokens from being stolen or reused on another device. |
| Real-Time Risk-Based MFA | Adjusts MFA requirements based on live threat intelligence. |
| Secure Hybrid Workforce Policies | Blocks sign-ins from high-risk unmanaged devices. |
| Continuous Authentication Monitoring | Detects suspicious behavior after login and triggers additional security checks. |
- Organizations using Microsoft Entra ID must enable these features to protect against session hijacking attacks. Explore Microsoft Defender for Cloud Apps
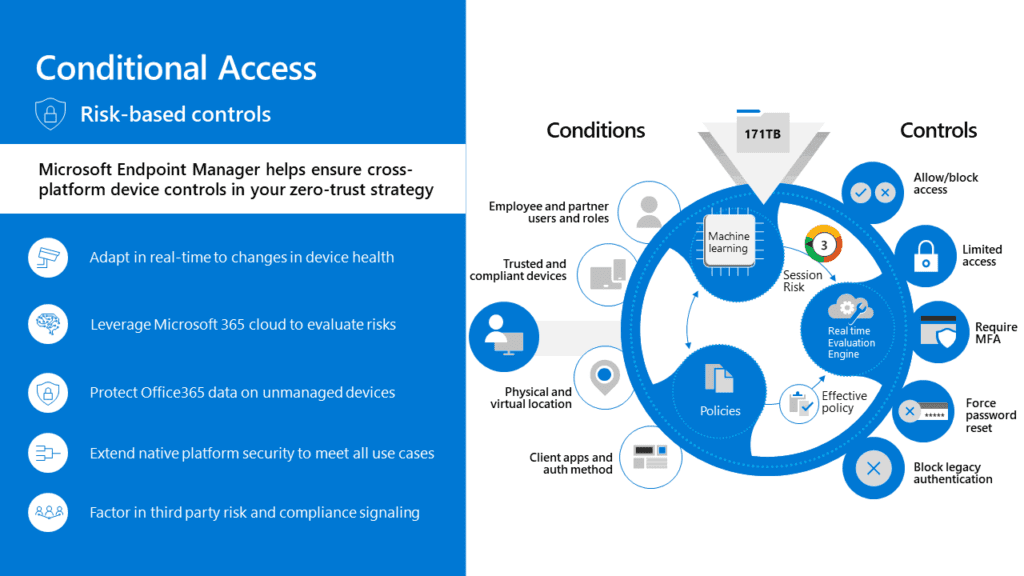
Step-by-Step: How to Secure Your Organization in 2025

1) Enable Microsoft Entra ID Conditional Access Policies
- What It Solves: Prevents attackers from using stolen session tokens by requiring extra security checks for risky sign-ins.
Key Conditional Access Policies:
- IP-Based Restrictions: Blocks logins from unknown or high-risk locations.
- Device Compliance: Allows only Intune-managed devices to access corporate resources.
- Risk-Based Authentication: Forces MFA or blocks access if a high-risk login is detected.
- Ensure Conditional Access is configured to require trusted devices and strong authentication methods.

2) Implement Zero Trust Access Controls for Microsoft 365
- What It Solves: Ensures only trusted devices and verified users can access sensitive data.
Key Zero Trust Measures
- Block sign-ins from unknown or unmanaged devices.
- Limit access based on device security posture.
- Enable continuous authentication monitoring for all high-risk accounts.
- Adopt a Zero Trust approach to identity security, requiring continuous verification. Read about the Zero Trust approach in our updated article on the Journey to Zero Trust.

3) Strengthen Phishing Awareness & User Training
- What It Solves: Reduces the chances of users falling for phishing emails that steal session tokens.
How Session Hijacking Works:
- How to identify phishing emails and fake login pages.
- The dangers of accepting pop-ups about certificate errors.
- Why multi-layered security is necessary—even with MFA.
- Regular security awareness training helps prevent credential theft.
What’s Changed Since 2022?
In 2022, we warned that MFA alone wasn’t enough. In 2025, the risks have evolved—but so have the solutions.
| 2022 Risks | 2025 Solutions |
|---|---|
| Session hijacking bypassed MFA | Token Protection for Microsoft 365 prevents token reuse |
| Stolen credentials enabled account takeovers | Real-Time Risk-Based MFA detects unauthorized logins |
| Phishing attacks targeted users | Zero Trust policies enforce device compliance before granting access |
| Conditional Access was underused | More organizations are implementing risk-based authentication |
- The journey to Zero Trust security is ongoing—make sure your Conditional Access strategy is up to date in 2025.
Summary: Strengthening Your Zero Trust Security Strategy
- MFA alone is not enough—session hijacking bypasses authentication security.
- Conditional Access is critical—it blocks attackers using stolen tokens.
- Network defenses & phishing awareness reduce the risk of stolen credentials.
- Microsoft Entra ID Conditional Access policies offer fine-tuned security control.
- Adopt a Zero Trust model—require device compliance and risk-based authentication.
Secure Your Business from MFA Bypass Attacks
Cyber threats continue to evolve, and so must your security strategy. If you haven’t reviewed your Microsoft Entra ID security policies, now is the time.



