Ready to move beyond on-premises domain controllers? Learn how to retire Active Directory and secure your server infrastructure using Entra ID, Azure Arc, and modern cloud-native identity strategies.
Utilizing Microsoft Entra ID & Azure Arc for a Modern Identity Strategy
For over 30 years, Active Directory (AD) has been the backbone of enterprise identity and access management. But with today’s shift toward cloud-first security models and SaaS applications, organizations are re-evaluating legacy domain dependencies.
While many have migrated user identities and devices to the cloud, on-premises servers often lag behind—still reliant on domain joins and traditional group policies. Microsoft now recommends retiring AD in favor of modern solutions like Microsoft Entra ID and Azure Arc, which offer stronger controls such as Zero Trust, Privileged Identity Management (PIM), and risk-based access policies.
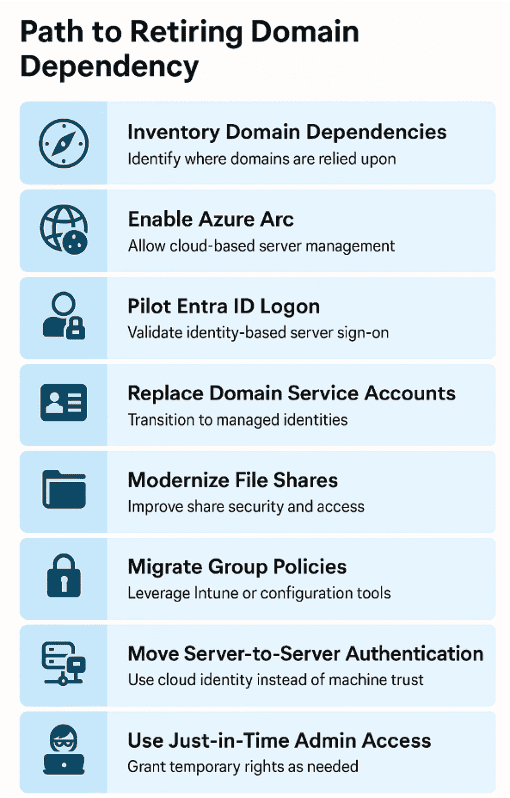
The Path to Retiring Domain Dependency is a series of steps that allows you to evaluate, plan, and mitigate dependencies with a thoughtful approach that delivers value with each step. While these steps are somewhat ordered, not all journeys are the same and modification may be needed depending on special circumstances. We will be utilizing two core tools to support this migration but there are many capabilities that we can take advantage of along the way.
Below is a step-by-step modernization framework to help your organization phase out Active Directory and transition to secure cloud identity.
Core Tools for Transition
Microsoft Entra ID
A modern cloud identity platform supporting:
- Role-based access control
- Risk-based Conditional Access
- Multi-Factor Authentication (MFA)
- Privileged Identity Management (PIM)
Azure Arc
Extends Azure management to on-premises or hybrid servers:
- Enables policy enforcement and tagging
- Facilitates secure server access without VPNs
- Supports managed identities and Azure-native tooling


Step-by-Step Migration Strategy
Step 1 — Identifying Domain Dependencies
The first step in the plan is to build your plan.
Nobody likes an assessment but at the end of the day, we can plan until we know the details and interdependencies of every service the servers themselves are designed to support.
With a combination of documentation, manual inspection, and data driven tools like Quest Software and Azure Dr. Migrate, we can effectively get our arms around how the workloads in each domain or domains interact. Allowing us to begin to prioritize the timeline service line by service line for the greatest impact.
Pro Tip: Map out interdependencies across services to reduce surprises during decommissioning.
Step 2 — Enabling Azure Arc
Deploying Azure Arc to the environment implements the bridge between Entra/Azure capabilities and servers that are on-premises or operating in other cloud/colocation environments. Azure Arc is our control plane for the following:
- Applying tagging and policy to allow for server management
- Establishing the control-plane between the cloud and server (Windows or Linux)
- Enabling other capabilities such as updates, patching, auditing, etc.
By simply Arc-enabling our servers, we establish a secure management point between Azure-based capabilities and traditional Windows servers wherever they reside.

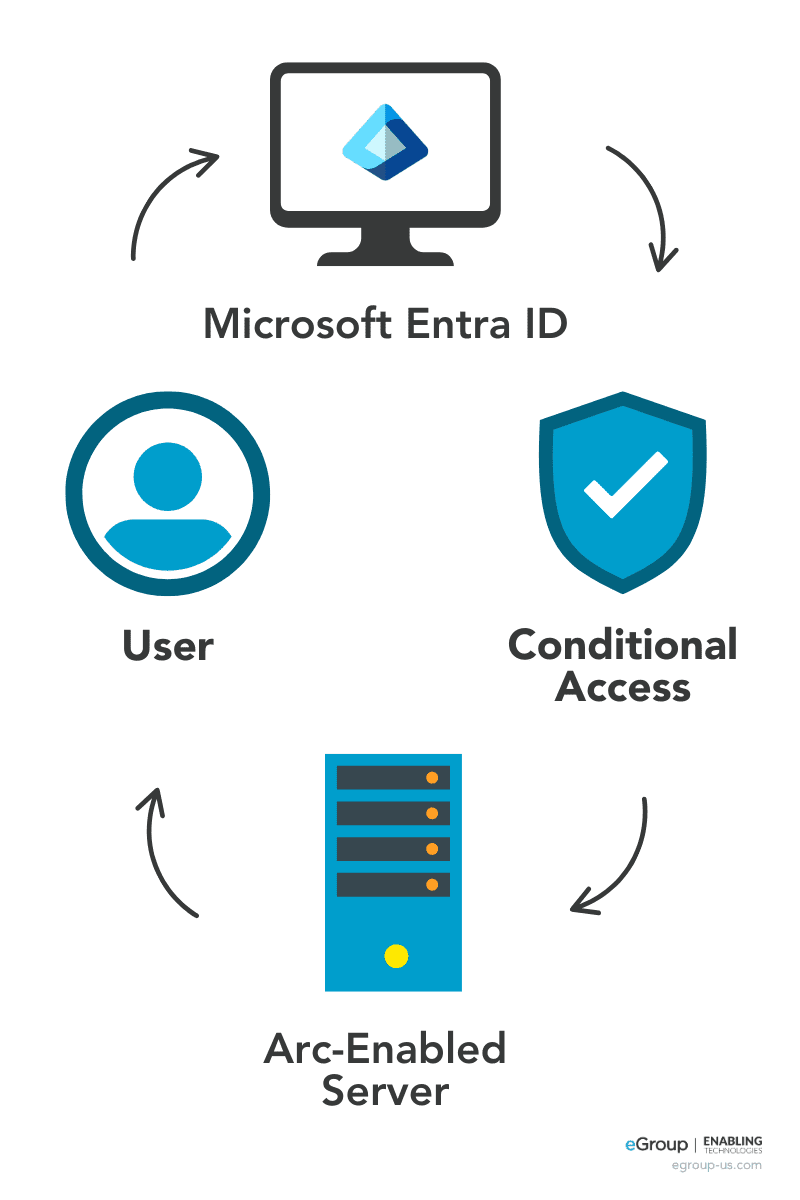
Step 3: Configuring Entra ID for Server Access
Getting to the fun part. How do we manage our servers with Entra ID and not have a domain or local account? This is where Azure Arc and Entra ID work together.
The user initiates a connection to an on-premises server. Entra ID authenticates the user based on the risk-based conditional access policies in place.
Once authenticated, Azure Bastion establishes the secure RDP/SSH session to the Arc-enabled resource without exposing any public ports or networks.
The administrative user can perform their tasks securely over a private network without solutions like VPN or third-party remote access solutions.
Step 4 — Replacing Service Accounts for Managed Identities
Privileged access isn’t limited to human administrators—it also includes service accounts used by critical systems like IIS, databases, and backup tools. These accounts often run with elevated privileges and pose a security risk if unmanaged.
Unlike the integration accounts discussed in Step 7 (used for inter-system communication), the goal here is to replace domain-based service accounts with managed identities for enterprise applications that “run as” specific users.
To achieve this, you can use:
- System-assigned managed identities – Automatically created and bound to a specific Azure Arc-enabled server. These provide secure authentication without needing to store or manage credentials manually.
- User-assigned managed identities, Entra ID App Registrations, or Service Principals – Suitable for scenarios that require shared identities or broader reuse across services.
By leveraging these identity types, you can strengthen security and eliminate the risks tied to traditional domain service accounts.


Step 5 — Modernizing File Share Security and Access
Legacy Windows File Shares remain one of the most vulnerable targets for ransomware in enterprise environments. To reduce risk and modernize access, organizations should segment file storage into distinct categories:
- User documents → Migrate to OneDrive
- Departmental files → Centralize in SharePoint Online, Teams, and OneDrive
- Application files → Transition to Azure File Shares
The key to this approach is eliminating traditional Windows File Shares in favor of modern platforms that support Entra-based access control lists (ACLs). This enables:
- Enhanced risk-based conditional access
- Improved compliance and data governance
- Stronger defense against ransomware propagation
By shifting file access to cloud-native platforms with Entra integration, you gain both flexibility and control—essential for securing sensitive data and maintaining business continuity.
Step 6 — Migrating Group Policy
If you’ve ever said, “Group Policy is a mess,” you’re not alone. Over time, Group Policy Objects (GPOs) tend to accumulate without clear governance—leading to conflicting rules and unpredictable outcomes on server objects.
Modern environments benefit from replacing GPOs with cloud-aligned solutions such as:
- Microsoft Intune – Ideal for device and endpoint policy management
- Desired State Configuration (DSC) – Enables declarative configuration of systems
- Azure Policy for Arc – Extends governance to hybrid servers
These tools provide greater visibility, auditability, and control over policy enforcement. With DSC specifically, a range of third-party platforms can automate deployment using pre-defined configuration blueprints—streamlining operations and ensuring compliance with your desired state.


Step 7 — Transitioning Server-to-Server Authentication
In traditional three-tier architectures (Web → API/Service Layer → Database), inter-server communication is often secured using domain-based service accounts. While common, this approach creates dependencies on domain trust and increases risk exposure.
To modernize and secure these interactions, organizations should replace service accounts with token-based authentication using Microsoft Entra App Registrations. This enables:
- App-to-app authentication without machine-level domain trust
- Stronger security controls and visibility into inter-service communications
- Reduced attack surface by eliminating legacy service account credentials
This shift enhances identity management and enforces zero trust principles across critical application layers—strengthening your overall security posture in hybrid or cloud-native environments.
Step 8 — Enable Just-in-Time Admin Access
Just-in-Time (JIT) access, powered by Entra ID Privileged Identity Management (PIM), brings cloud-native privilege controls to server environments. Instead of always-on admin rights, administrators are granted “eligible” access to critical systems and can elevate permissions only when needed.
This approach ensures that:
- No credentials hold standing admin rights during normal operations
- Elevations require approval and are auditable, following a workflow you define
- Attack surface is minimized, as even compromised credentials can’t act without elevation
By requiring an explicit, monitored process for privilege escalation, PIM strengthens Zero Trust principles—every access attempt is evaluated and justified. In effect, it would take multiple compromised accounts to bypass this model, greatly increasing security.


Additional Step — Segment Legacy Domain-Dependent Systems
For applications that still require domain connectivity, it’s critical to segment and secure these environments to reduce exposure. Leverage software-defined networking (SDN) to explicitly define:
- Which systems can communicate
- What protocols and ports are allowed
- How traffic is inspected and controlled
This isolation strategy minimizes the blast radius if a legacy system is compromised, ensuring that outdated dependencies don’t jeopardize your broader environment. By applying granular access controls and microsegmentation, you enhance security while maintaining necessary functionality for domain-bound applications.
Final Thoughts: Take the First Step Toward Domain Retirement
Retiring Active Directory isn’t an overnight change—it’s a strategic evolution toward secure hybrid environments. Microsoft’s guidance and tooling—especially Entra ID and Azure Arc—enable you to move forward with confidence.
Beyond improved security, this journey unlocks:
- Streamlined patching and updates
- Centralized management
- Simplified compliance


Ready to Modernize Your Identity Strategy?
Let eGroup help you retire your legacy AD domains with confidence.
We’ll guide you through discovery, planning, and implementation with a roadmap tailored to your current infrastructure.



