See: Table of Contents
Privileged Identity Management and Privileged Access Management

Protecting privileged accounts is essential in a Zero Trust world. Learn how Privileged Identity Management (PIM) and Privileged Access Management (PAM) strengthen security, enforce least privilege, and reduce insider threats.
Privileged Identity Management (PIM) and Security Controls
Privileged Identity Management provides critical security controls to safeguard privileged accounts such as service accounts, passwords, SSH keys, and digital certificates that hackers often target as attack surfaces for various criminal acts such as data breaches.
PIM helps prevent mismanagement of privileged access by automating its process and ensuring compliance with industry standards and regulations. Utilizing predefined workflows, PIM checks whether authorized identities can assume roles for an extended duration and whether any privileges granted have expired.

Zero Trust and Cloud Architectures
Privileged access management (PAM) is an essential component of any cybersecurity strategy, providing organizations with a means to monitor, oversee, and control elevated privileges granted to users within their IT environment. PAM serves as an invaluable shield against insider threats, external breaches, and complex cyberattacks that pose potential danger to any organization.
Modern enterprises recognize the importance of adopting a Zero Trust architecture with Privileged Identity Management at its core. One effective method for realizing such an architecture is through the implementation of Microsoft Entra ID with Privileged Identity Management (PIM), which integrates just-in-time access controls, continuous monitoring, and adaptive policies to enhance security and enforce a true Zero Trust model.
Implementing a privileged access management solution enables organizations to apply the least privilege principle, which limits cyberattack opportunities by granting users only the necessary privileges for their tasks.
Another key advantage of Privileged Identity Management solutions is the ability to create logs of all activities associated with privileged accounts, which provides invaluable data to security teams when investigating incidents.
Microsoft Entra ID with Privileged Identity Management (PIM) integrates seamlessly with identity and access management platforms to provide comprehensive visibility into privileged identities and their associated permissions, offering robust tracking and monitoring capabilities to enhance security and compliance.
Summary: Privileged Access Management (PAM) plays a crucial role in securing IT environments by controlling, monitoring, and limiting privileged access. A Zero Trust approach ensures that privileged access is granted only under strict, fine-grained conditions and for the shortest necessary duration.
Key Takeaways:



Administrator Account Management

Administrator or superuser accounts allow users to gain unrestricted access to files and directories they require for their jobs, such as root or Administrator on Unix/Linux systems or Administrator on Windows systems. With access to these credentials such as root/Administrator access they are able to take actions on enterprise assets that ordinary end-users cannot; for instance installing software programs, changing network configuration settings, adding or deleting data, altering database or server settings etc. Privileged identity management aims at making sure these accounts are carefully managed so their activities do not pose risks to enterprise security.
One way PIM protects superusers is through two-factor authentication and other forms of multi-factor authentication for these accounts. Furthermore, PIM limits what a superuser can do with their privileges by employing automated policies to monitor and limit access. Such controls help avoid human mistakes as well as malicious insider activity that are common causes of data leakage.
PIM also plays an integral part in managing privileged accounts by providing users with the capability of revoking role access when no longer necessary, thus eliminating an attack vector. You can set maximum activation durations and require that any time an administrative task needs to be performed, justifying its activation prior to performing said task.
PIM will notify administrators if a superuser does not log off after performing administrative tasks, warning that there is still an active session using his or her account and privileges, encouraging the user to log off as soon as possible in order to prevent unintended privilege escalation by anyone else.
PIM serves as a central repository for discovering and administering all your privileged accounts across systems, devices, applications and databases. By centralizing administration of your privilege accounts across systems, devices, applications and databases, this centralized approach makes it possible to implement and enforce least privilege principles – an essential requirement of many compliance standards such as FISMA, HIPAA, PCI DSS and Sarbanes-Oxley regulations.
Administrator or superuser accounts allow users to gain unrestricted access to files and directories they require for their jobs, such as root or Administrator on Unix/Linux systems or Administrator on Windows systems. These accounts allow privileged actions that ordinary end-users cannot perform, such as:
- Installing software
- Changing network configurations
- Adding or deleting data
- Altering database or server settings
Privileged identity management ensures these accounts are carefully managed so their activities do not pose security risks.
Key Security Measures in PIM for Superusers:
- Multi-Factor Authentication (MFA): Requires additional authentication for superuser accounts.
- Automated Policy Enforcement: Limits what a superuser can do with their privileges.
- Session Monitoring: Sends alerts if a superuser fails to log off after administrative tasks.
- Centralized Privileged Account Management: Provides a single repository for managing privileged identities across systems, devices, and applications.
Cloud Access and Privileged Identity Management
As businesses transition more of their business applications to the cloud, privileged accounts must be managed properly to reduce risk and ensure users who require access don’t accrue unnecessary privileges. Privileged Identity Management (PIM) solutions offer many capabilities designed specifically to tackle this challenge.
PIM integrates with directories, cloud platforms and business applications to identify privileged identities enterprise-wide. Once identified, PIM solutions use role policies based on the principle of least privilege to assign roles based on eligible or active criteria – for instance eligible roles are only activated when necessary to complete a task and require justification or active roles give out privileges without manual approval – providing flexibility when managing privileges within organizations.
PIM solutions also enable dynamic privilege access that grants only what’s necessary, limiting potential security breaches while simplifying monitoring and auditing privileged account activity. In addition, PIM can offer various privilege escalation alerts in case of unusual user behaviour.
Integration between PIM solutions and existing systems, particularly identity and access management (IAM) platforms is another key feature of a PIM solution, enabling agencies to more easily enforce Zero Trust principles while applying the principle of least privilege across their organization. This makes PIM solutions much simpler to use when managing users.
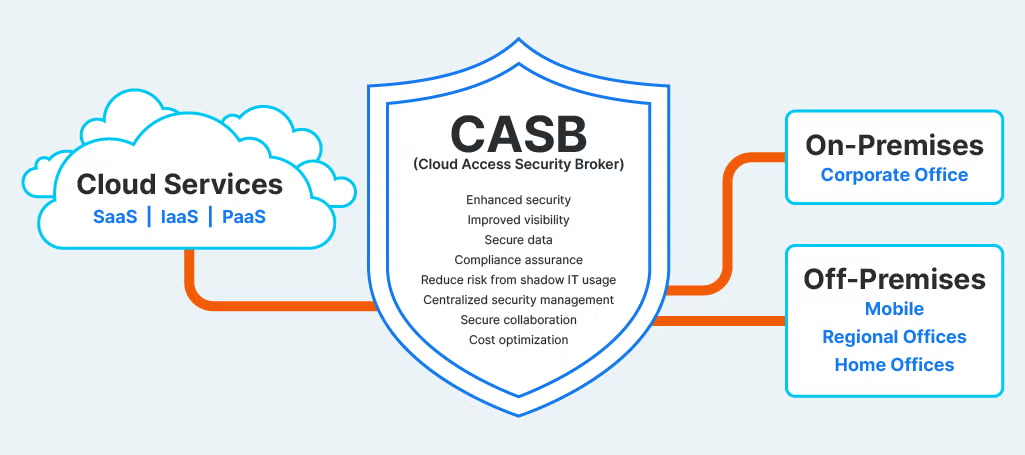
PIM solutions can also integrate with Cloud Access Security Brokers (CASBs) for greater visibility and control over cloud application use. A CASB can autodiscover all of the third-party cloud apps an organization has deployed, assessing their level of risk based on how they’re being used and what type of information is contained within them. Furthermore, a CASB can enforce governance policies to help safeguard both data stored within these cloud services as well as any intellectual property stored there by restricting who can access applications while tracking all activity within them.
As businesses transition more of their applications and services to the cloud, privileged accounts must be managed properly to reduce risks.
Key PIM Features for Cloud Access:
- Role-Based Access Controls (RBAC): Assigns privileges based on eligibility criteria.
- Just-in-Time Privileges: Grants access only when necessary and requires justification.
- Dynamic Privilege Escalation Alerts: Identifies unusual activity and potential security breaches.
PIM solutions integrate with Cloud Access Security Brokers (CASBs) to provide visibility into third-party cloud applications, assessing risk levels and enforcing governance policies to safeguard data.
Securing Controlled Information Properly
Privileged identity management and PAM solutions can be powerful tools in any cybersecurity leader’s toolbox, but only when used effectively can their full value be realized and security incidents avoided. When these tools are misutilized, attackers could exploit privileged identities that have not been secured sufficiently in order to penetrate company perimeters and gain unfettered access to critical assets.

PIM and PAM solutions allow organizations to more accurately allocate privileges by only giving elevated access when it is essential for job performance, thus limiting attack surfaces and mitigating risk. Furthermore, security teams can track activity associated with privileged accounts and roles for compliance auditing purposes or mitigating risk mitigation purposes.
These solutions offer a centralized dashboard to monitor all user accounts, including those with administrative privileges, and automatically revoke access when employees leave or change job roles. Furthermore, time-bound permanent roles replace the practice of assigning roles directly and setting reminders to revoke them after a set period; providing more secure approaches with real controls that prevent security gaps from manual assignments of privileges.
Furthermore, these systems can support a “just-in-time” privilege model which enables temporary privileges that become active only when necessary – rather than being granted permanently to an identity – helping reduce risks of privilege misuse or abuse and supporting investigations through its capabilities of recording and replaying account usage sessions for further evidence collection.
Implementing a robust PIM strategy should be part of every cybersecurity program and should include regular awareness training on its use to reduce cyber incidents. When embarking upon PIM implementation or have already deployed it, make sure to partner with an experienced IT consulting firm in order to optimize and maximize its value.
Key Benefits of PIM and PAM Solutions:
- Prevents permanent privilege assignments by using time-bound access.
- Tracks and records privileged account usage for security investigations.
- Supports Zero Trust principles by requiring continuous validation before granting access.
- Reduces insider threats by ensuring strict monitoring of privileged accounts.
Additionally, these systems support a “just-in-time” privilege model, ensuring that privileges are activated only when required rather than being permanently granted, reducing the risk of privilege misuse.
Final Thoughts
Implementing a robust Privileged Identity Management (PIM) strategy is essential for securing modern IT environments. Organizations must integrate PIM solutions with Zero Trust security models to minimize attack surfaces and ensure compliance with regulations like FISMA, HIPAA, PCI DSS, and Sarbanes-Oxley.



