In the last article, I provided an overview of Microsoft’s Secure by Default framework for Microsoft Purview, designed to help organizations implement basic data governance and security controls quickly. Today, we’ll dive into the first foundational phase of this framework.
This blog assumes familiarity with Purview sensitivity labels and Data Loss Prevention (DLP) policies. Additionally, it assumes that Secure by Default settings are first applied to a pilot group before expanding organization-wide.

Overview of Phase 1 Actions
- Apply a default Information Protection (sensitivity) label to all new or edited documents, restricting access to internal users only.
- Require users to modify the default label if they need to share or email documents externally.
- Enable Data Loss Prevention (DLP) policies to block externally shared or emailed documents unless appropriately relabeled.
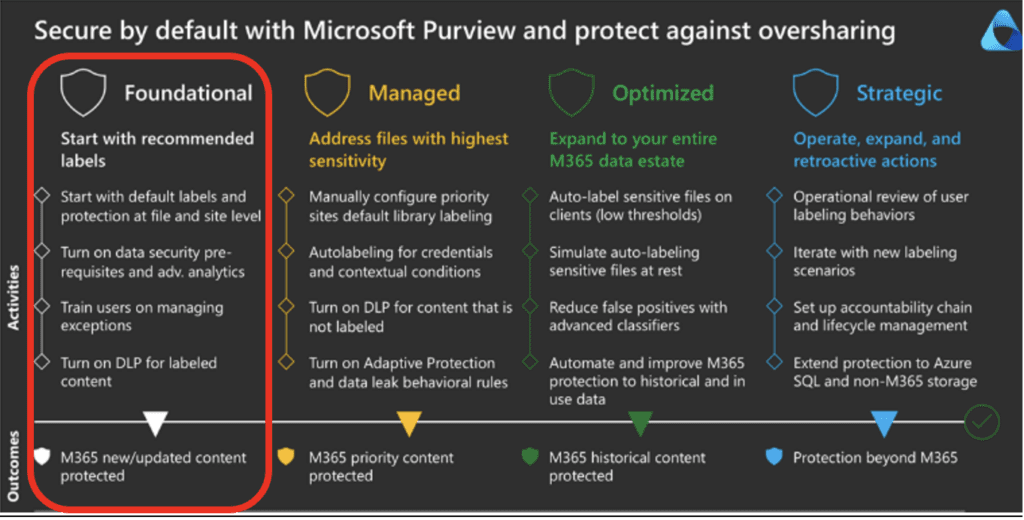
Desired Phase 1 Outcomes
1. Users are quickly introduced to Purview controls
- Employees learn to interact with sensitivity labels, ensuring smoother adoption in later phases.
- Increased awareness of governance policies makes future data security measures easier to implement.
2. Documents are protected by default
- New and updated files cannot be shared externally unless relabeled.
- Security teams receive alerts when users downgrade labels to share files.
- All label changes are logged, ensuring compliance and oversight.
3. Users become intentional about external sharing
- Manual label changes are required to share a file externally.
- DLP automatically blocks unapproved external sharing, prompting users to justify label downgrades.
- Audit logs track sharing activity for security and compliance visibility.

Label Configuration Guidance
Microsoft recommends the label/sublabel taxonomy outlined here. While this is solid guidance, you may not need as many labels as suggested. In many cases, it makes sense to start with fewer labels and expand as needed. If you choose to follow Microsoft’s parent label structure, configure and publish at least the following to your pilot group:
| Label | Definition & Usage |
|---|---|
| Public | For unrestricted, public-facing content (e.g., published financials, press releases). |
| General | Default label for internal business data. Allows controlled external sharing. |
| Confidential | For sensitive business data. Encryption restricts access to internal users only. |
| Highly Confidential | Critical business data. Encryption limits access to explicitly named recipients. |

Training & Communication Plan for Pilot Users
Before automatically applying labels, it’s critical to educate the pilot group:
- Demonstrate how to apply labels in Microsoft 365 apps (including mobile).
- Show users what blocked emails or OneDrive/SharePoint sharing attempts look like.
- This is in the event they do not re-label a file but do try to share it externally.
- Clarify when and why files should be relabeled.
- Establish a feedback loop for user experiences, ensuring policy adjustments can be made.
- This is critical so that unexpected challenges or issues can be addressed promptly and the pilot team can perform their tasks efficiently, even with the new labeling and DLP requirements.
- Optional: Require users to provide a reason for label downgrades, which is logged for compliance tracking.
Enforcing DLP Policies for Confidential Data
Once labeling policies are in place, Data Loss Prevention (DLP) policies should be activated:
- Phase-in approach: Consider using warnings or tooltips first, before fully blocking external sharing.
- User Communication: Notify the pilot group well in advance before strict enforcement begins.
- Feedback Monitoring: Closely track user responses and policy effectiveness post-implementation.

Next Steps: Scaling Phase 1 & Preparing for Phase 2
Once the new Purview labels and policies have been fully implemented, it is important to allow time for adjustment before applying the Phase 1 settings to a broader group or introducing Phase 2 restrictions to the Pilot group. Gathering feedback and conducting follow-up training for impacted staff is critical to documenting lessons learned and building support for further data governance buy-in.
Use the Activity Explorer in the Purview management portal to review and gather metrics on labeling and DLP activity. This data provides insight into how the Secure by Default effort is progressing and helps identify any anomalies or unexpected impacts.
In my next installment, we will dive into the additional requirements and benefits of Phase 2 of the Secure by Default Framework.
Phase 1 Implementation: Key Next Steps
Once Phase 1 is fully implemented:
- Allow time for user adaptation
- Gather activity insights from Purview’s Activity Explorer.
- Conduct follow-up training based on user feedback.
This will inform the rollout strategy for the broader organization and prepare teams for Phase 2 of Secure by Default.
Final Thoughts
Implementing Purview Secure by Default Phase 1 ensures that data protection becomes second nature for employees, while organizations establish baseline security policies without disrupting productivity.
Looking ahead, Phase 2 will introduce automated sensitivity labeling and stronger DLP enforcement—stay tuned for the next blog!
Need help implementing Purview Secure by Default? Contact eGroup today to explore how we can support your Microsoft Purview strategy.








